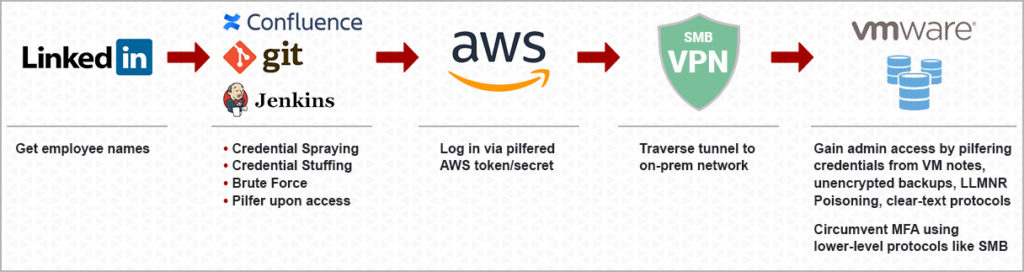
Credential Attacks

Attackers Don’t Hack In… They Log In.
In today’s world, credentials are the easiest way for attackers to breach your defenses. Why spend time exploiting vulnerabilities when they can just log in as you?
We’ve seen this play out time and time again. Attackers harvest credentials, gain access, and expand their foothold—all while appearing like legitimate users. Traditional tools—firewalls, EDR, scanners—aren’t built to detect these kinds of attacks. And the costs are staggering.
Download the WhitepaperCredential attacks are a critical enabler for ransomware, costing businesses over $10 billion in the past five years
0%
of hacking-related breaches involve brute force or stolen credentials.
Verizon Data Breach Investigations Report (DBIR)
0%
of financial sector attacks leverage credential stuffing, the most common attack vector against the industry.
FBI private industry notification on credential stuffing attacks.
0%
of companies have over 500 accounts with passwords that never expire.
Varonis Data Risk Report
0%
of people use the same
passwords for both work and personal accounts.
The Password Pandemic Whitepaper
The Password Pandemic
Watch our roundtable discussion, "Tech Talk: The Password Pandemic," where experts delve into the challenges of credential-based attacks and the strategies to combat them.
Defense Alone Isn’t Enough. Fix What Matters.
Credential attacks are growing more sophisticated and more costly. Are you ready to see your vulnerabilities from the attacker’s perspective?
Get a Demo of NodeZero®
Find out how Horizon3.ai can uncover your weaknesses—and empower you to fix them before attackers exploit them.
