Ransomware Impact
Ransomware is an increasingly common and lucrative attack.
Ransomware attacks have become democratized, with criminal groups establishing Ransomware-as-a-Service (RaaS) operations, renting ransomware to recruited affiliates that, in turn, run attacks against organizations and pay a “royalty” to the RaaS providers.
Active Directory Enumeration
SMB Share Enumeration
Credential Dumping
Encryption of SMB shares
Encryption of VMWare ESXi virtual machines
Wiping/Reformatting
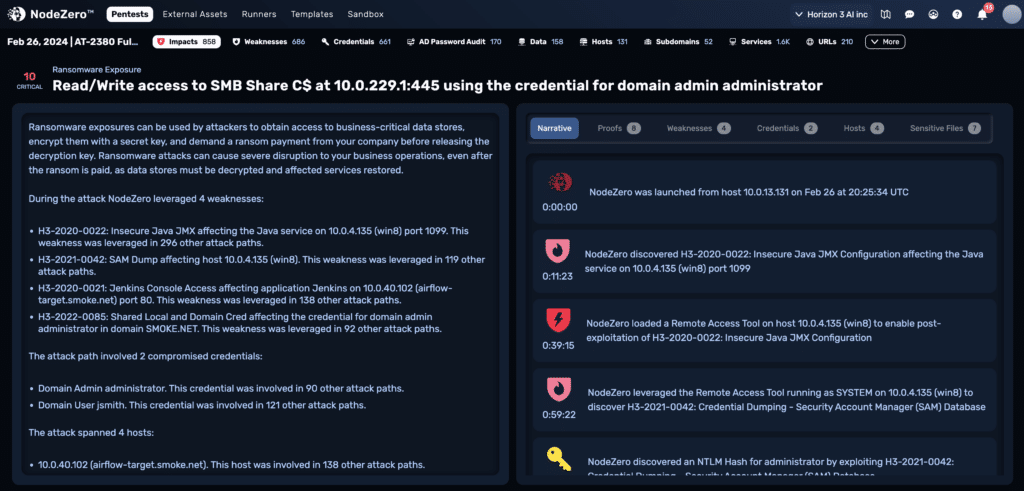
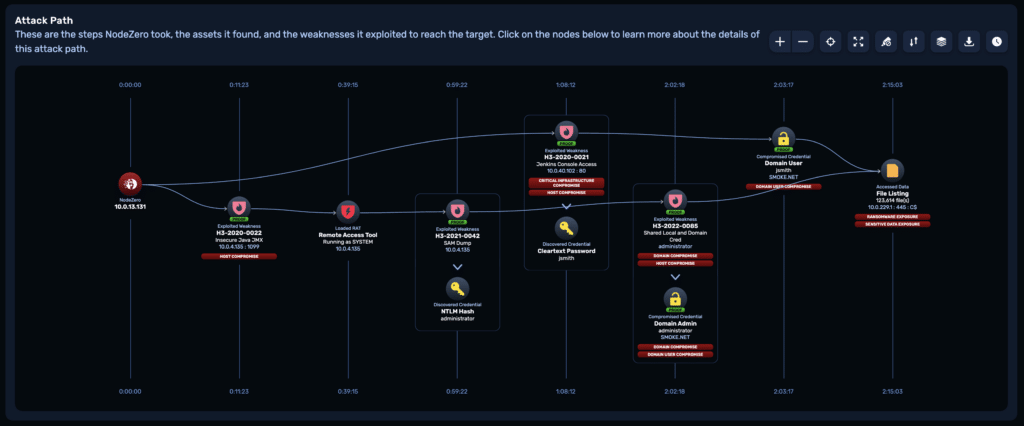
In a ransomware attack, like a data theft attack, criminals infiltrate a company’s network and then move laterally to identify sensitive business data. Initial access to the network often comes from compromising a legitimate credential. Instead of simply stealing a copy of the data, however, they encrypt it and demand payment in cryptocurrency before providing a decryption key. Starting with a compromised credential, the ransomware conducts:
How do you assess Ransomware risk?

The ransomware threat landscape has changed: here’s how defenders must adapt.
What can NodeZero tell you?
Run NodeZero and inject it with a “compromised” domain user credential.
NodeZero will then use this domain user credential to:
Including SMB shares