Vulnerable ≠ Exploitable
Ever wonder how much of your time and effort is being wasted fixing things that don’t actually matter?
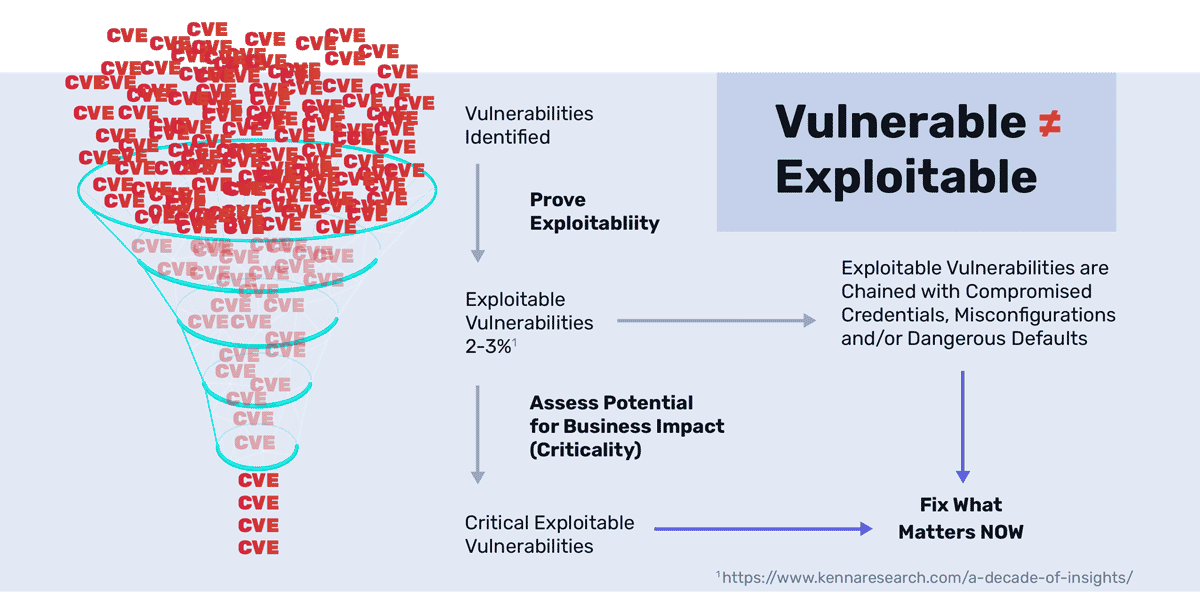
You may be surprised to hear that a large majority of all vulnerabilities are unexploitable. According to data compiled by Kenna, in 2020, only 2.7% of the vulnerabilities found appeared to be exploitable and only 0.4% of those vulnerabilities were actually observed to be exploited at all.
Traditional agent-based vulnerability scanners and simplistic port-scans aren’t enough.
Create too much noise
Ignore how attackers actually think
Provide no prioritization
So how do you know if it is critical to fix what you find?
The hardest part of cyber security is deciding what NOT to fix.
Spending valuable and scarce time and effort on remediating weaknesses that are not exploitable or do not represent a substantial business impact is itself a risk. Find out more about how to prioritize vulnerabilities in this whitepaper.
Criticality begins with the exploitability of a weakness.
There are many reasons why a reported critical finding from vulnerability scanners and some pentesters may not be exploitable or would be very difficult to exploit, hence do not truly impose much or any risk.
No exploit exists
There is no existing exploit available for the vulnerability
Outdated ≠ exploitable
In the absence of a specific vulnerability, software being merely outdated/obsolete does not pose a critical risk.
Network context
The context of where the vulnerable asset is in the network makes the risk informational rather than critical.
High complexity
Several complex and/or impractical conditions must be met for the
vulnerability to be exploited by an attacker.
Not accessible
The vulnerability exists in a part the software that isn’t accessible from the attacker’s perspective.
Component not in use
The suspected software doesn’t necessarily run in a vulnerable configuration.
Target End State: Proactive Security Posture
Security Controls
Are you ready to respond to Ransomware? If APT29 is targeting your sector, can you detect and disrupt their known tactics, techniques, and procedures?
So what do you do? Where do you start? From our experience as former CIO’s, the best approach is a Catch Up, Keep Up, and Stay Ahead plan.
A Future of Continuous Security Assessment
Over the last decade, more and more CVEs/vulnerabilities are being found and reported, making it very hard to keep pace. It’s snowballing and creating fatigue.
With an annual manual pentest, you have giant craters in your security posture that develop between cycles as critical vulnerabilities come out; systems change with new software, patches and hardware; and personnel turns over.
How can NodeZero help you?
Let our experts walk you through a demonstration of NodeZero, so you can see how to put it to work for your company.

